Apache Tika Security Flaw (CVE-2025-66516)
-
Dear community,
The CVE-2025-66516 describes an XXE (XML External Entity injection) vulnerability in Apache Tika. It can be exploited when Tika processes PDFs containing specially crafted XFA (XML Forms Architecture) content.
Following the CVE publication and analysis, we performed a full identification of all Tika dependencies within the GoFAST ecosystem:
- CEO-Vision executable (embedded binary)
- Alfresco (transformation component)
- Solr (extraction module "SolrCell")
This post provides a retrospective of the analyses performed and the actions taken by our security committee to address this vulnerability.
References:
 ️ Embedded CEO-Vision Tika executable
️ Embedded CEO-Vision Tika executableEven though the embedded executable is not directly exposed and is only used after multiple control layers (application stack, security filtering, antivirus scans, etc.), it was immediately handled within our security pipeline.
As a result:
- The embedded Tika component was immediately updated through a dedicated security patch, progressively deployed to all supported GoFAST Enterprise production environments without requiring any service interruption.
- The fix has been integrated into the current GoFAST security release 4.4.1 and will also be included in upcoming versions.
 ️ Tika dependencies in Alfresco
️ Tika dependencies in AlfrescoThe Alfresco Content Services Community Distribution may embed Tika dependencies that require updates in certain setups.
However, the GoFAST core component Alfresco Repository is not impacted, as it has no longer performed content extraction internally since version 7.0.
The impacted Alfresco component is Alfresco Transform Core, used via T-Engine, which has not been installed or used in GoFAST since v4.
Document transformations are now handled directly by our embedded applications, mainly for performance reasons (OnlyOffice, LibreOffice, embedded Tika executable, etc.).
Attempting to activate the Alfresco transformer confirmed that the component is not loaded, as it is not present in our deployments:
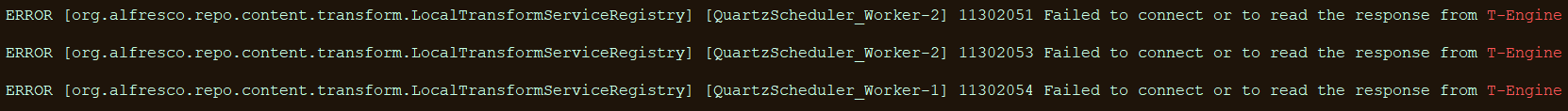
It has therefore been confirmed that the Alfresco CE integration in GoFAST is not vulnerable to CVE-2025-66516.
 ️ Tika dependencies in Apache Solr
️ Tika dependencies in Apache SolrApache Solr may also embed Tika dependencies that require updates in some configurations.
The vulnerability affects the extraction module (SolrCell), which is not used in our GoFAST integration of Apache Solr.
In GoFAST, content and metadata extraction has always been fully managed by our application stack (Alfresco, embedded Tika executable, etc.).
As a preventive measure, we still attempted to deploy the vendor-recommended mitigation for impacted environments, and confirmed that the extraction libraries are not even loaded in our case:
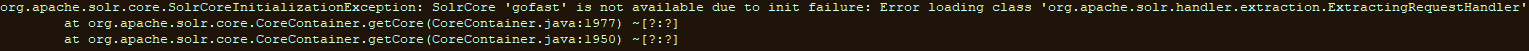
It has therefore been confirmed that the Apache Solr integration in GoFAST is not vulnerable to CVE-2025-66516.
 ️ Roadmap, Monitoring & Security Watch
️ Roadmap, Monitoring & Security WatchThe following roadmap has been defined for the two components that contain Tika dependencies but do not load them in our deployments:
- Alfresco Content Services Community components are scheduled for a major update in the next intermediate GoFAST release.
- Apache Solr is also scheduled for a major update in the next intermediate GoFAST release.
The CEO-Vision security committee continues to actively monitor:
- Vendor announcements (Apache, Hyland, RedHat, etc.)
- Hardening and mitigation recommendations
- Field feedback (CNA/NVD updates, OS security bulletins, etc.)
For GoFAST Enterprise administrators: if you are currently running an unsupported GoFAST version, we strongly encourage you to contact your Enterprise Support via the update ticket that was opened for you, in order to plan your upgrade as soon as possible.
Have a great day!
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login